Alas. I've been using Windows so long that now I go back to the Mac and want Ctrl-C to work. Sad, but there it is. At last I found Karabiner, which does keyboard remapping, and created a set of Karabiner rules to map the main Windows Ctrl-keystrokes to the matching ⌘-keystroke on Mac:
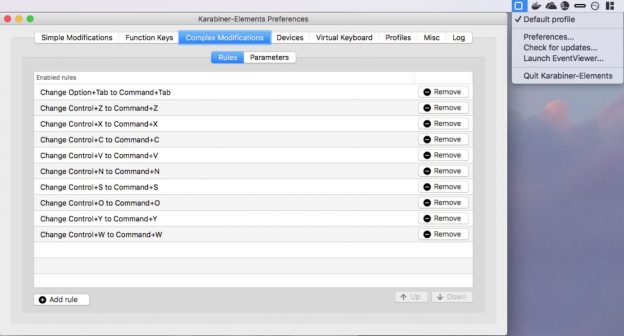
Okay, so Ctrl-W isn't strictly a windows keystroke. But who can work without Ctrl-W?
Karabiner Complex Rules Snippet
{
"profiles": [
{
"complex_modifications": {
"parameters": { /* ... etc ... */ },
"README": "********************************************************************************************************",
"README": "*" COPY JUST THE ELEMENTS OF THIS "rules" array into your profiles.complex_modifications.rules array. "*",
"README": "********************************************************************************************************",
"rules": [
{
"description": "Change Control+Z to Command+Z",
"manipulators": [ { "from": { "key_code": "z","modifiers": {"mandatory": ["control"],"optional": ["any"]}},"to": [{"key_code": "z","modifiers": ["command"]}],"type": "basic"}]
},
{
"description": "Change Control+X to Command+X",
"manipulators": [ { "from": { "key_code": "x","modifiers": {"mandatory": ["control"],"optional": ["any"]}},"to": [{"key_code": "x","modifiers": ["command"]}],"type": "basic"}]
},
{
"description": "Change Control+C to Command+C",
"manipulators": [ { "from": { "key_code": "c","modifiers": {"mandatory": ["control"],"optional": ["any"]}},"to": [{"key_code": "c","modifiers": ["command"]}],"type": "basic"}]
},
{
"description": "Change Control+V to Command+V",
"manipulators": [ { "from": { "key_code": "v","modifiers": {"mandatory": ["control"],"optional": ["any"]}},"to": [{"key_code": "v","modifiers": ["command"]}],"type": "basic"}]
},
{
"description": "Change Control+N to Command+N",
"manipulators": [ { "from": { "key_code": "n","modifiers": {"mandatory": ["control"],"optional": ["any"]}},"to": [{"key_code": "n","modifiers": ["command"]}],"type": "basic"}]
},
{
"description": "Change Control+S to Command+S",
"manipulators": [ { "from": { "key_code": "s","modifiers": {"mandatory": ["control"],"optional": ["any"]}},"to": [{"key_code": "s","modifiers": ["command"]}],"type": "basic"}]
},
{
"description": "Change Control+O to Command+O",
"manipulators": [ { "from": { "key_code": "o","modifiers": {"mandatory": ["control"],"optional": ["any"]}},"to": [{"key_code": "o","modifiers": ["command"]}],"type": "basic"}]
},
{
"description": "Change Control+Y to Command+Y",
"manipulators": [ { "from": { "key_code": "y","modifiers": {"mandatory": ["control"],"optional": ["any"]}},"to": [{"key_code": "y","modifiers": ["command"]}],"type": "basic"}]
},
{
"description": "Change Control+W to Command+W",
"manipulators": [ { "from": { "key_code": "w","modifiers": {"mandatory": ["control"],"optional": ["any"]}},"to": [{"key_code": "w","modifiers": ["command"]}],"type": "basic"}]
}
],
"README": "******************************************************************************************************",
"README": "******************************************************************************************************",
/* ... etc ... */
}
}
]
}
Editing the Keyboard Map
This approach didn't work for me. I'm not sure what I missed.
